 Complex cyberattacks cost a cyber-criminal a fair amount of money to create and carry out. And the costs are only rising. This has prompted many to return to old-fashioned email tricks to bring in some needed cash.
Complex cyberattacks cost a cyber-criminal a fair amount of money to create and carry out. And the costs are only rising. This has prompted many to return to old-fashioned email tricks to bring in some needed cash.
Complex state-on-state cyberattacks and hacking tools like those revealed by Wikileaks (where the CIA can turn TVs into covert eavesdropping tools) are not going away, but you don’t have to be an elite programmer and hacker to make money using ransomware or simply stealing data. Email can be used expediently and effectively.
Remember how, during Hillary Clinton’s campaign, campaign manager John Podesta’s email account was accessed by Russian hackers? Podesta opened a message that looked like a warning from Google and inadvertently completed a fake password-reset page. His email account was compromised and eventually published, revealing some embarrassing messages that hurt Clinton’s campaign.
In 2016, one out of every 130 emails were harmful. That’s a significant increase over 2015’s rate of one in every 230 emails.
Symantic researchers call this “living off the land,” or a return to basics. These more straightforward methods are surging ahead of the more complex “zero-days” attacks that you hear more about in the news. “Zero-Days” attacks exploit security holes discovered in networks, or coding web-based errors in devices like modems.
One of the methods that increased markedly in 2016 were macros (or mini-programs) embedded in Word or Excel documents. Because Marcos are designed to execute a series of commands – and aren’t confined to a particular document – they can be repurposed for nefarious intent.
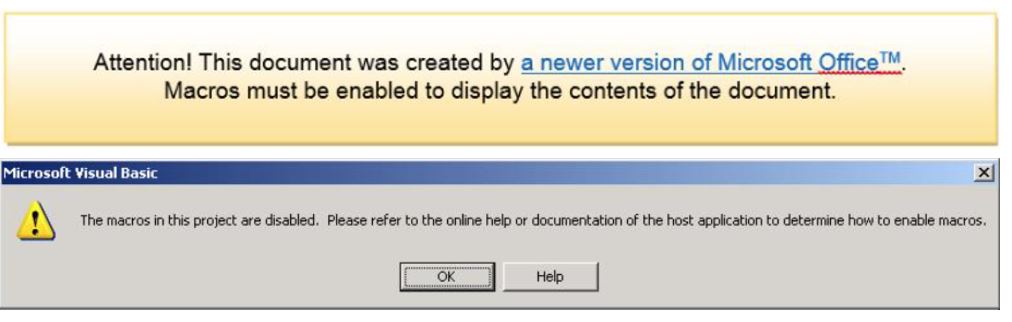
Macro malware was fairly common several years ago because macros ran automatically whenever you opened a document. In recent versions of Microsoft Office, however, macros are disabled by default. This means malware authors need to convince you to turn on macros so that their malware can run. They do this by showing you fake warnings when you open a malicious document.
So attackers now use “social engineering,” or tricks to convince victims to enable the cyberattack. For example, a Word document with a malicious macro might read:
Clicking on “OK” enables the malware.
It is very hard to detect an attack with it comes from a familiar platform like Microsoft. A good rule of thumb is to look at the email address from which the message was sent. If you don’t know it to be real, don’t open the document.
The resurgence of phishing and social engineering is likely a result of improvements in defenses by operating systems. It is getting tougher to fool a computer, but not so the user. Fancier attacks require more resources while sending thousands upon thousands of emails with malware is quick, simple, and often garners the amount of profit.
Users need to train themselves to stop clicking on dubious links and attachments. While this will likely only serve to force cybercriminals to move onto other methodologies, it reduces the likelihood of being a victim in this iteration of cyber attacks.

0 Comments