Ransomware, a type of malicious software designed to block access to a computer system until a sum of money is paid, is a pandemic spreading across the world affecting all types of organizations. Ransomware payments are typically made via anonymous bitcoin transactions – where ransoms can cost anywhere from $500-$2,000 to unlock an average PC.
The impact is spiraling to enormous levels and data collected by the FBI suggests that ransomware payments could reach more than one billion dollars this year. Even with the FBI’s research, it remains hard to scope the full scale of the problem because of the anonymity of cybercriminals and the difficulty of knowing precisely how many anonymous payments have been paid.
This graph above shows a clear exponential spike in activity in a very short period of time. What’s worse is that we don’t yet know how big this will be, or when the spike ends, because each public ransomware payment is only encouraging cyber-attackers to introduce new strains of malware and redouble their efforts. 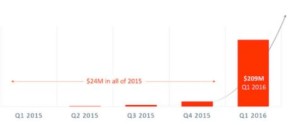
Reports of ransomware originate from everywhere and everyone in all industries. Cybercriminals do not discriminate, but they do prey on the weak – and the reality is that if your organization is unprepared, it’s likely you’ll become just another statistic. The situation sounds desperate, but a way for organizations to fight back against these types of cyber-attack effectively does exist.
How ransomware can be fought
One organization that has not taken a ransomware attack lying down is S.J. Louis Construction is a US-based construction contracting company that provides underground utility, tunneling, horizontal directional drilling, rock trenching and infiltration, and earthwork services to public and private markets. The company was founded in 1983 and is based in Rockville, Minnesota. Earlier this year, the organization had all of its current contract work and all previous project files crypto-locked by hackers who demanded $100,000 to return access to its data.
The breach encrypted $200 million worth of future project data. The preparedness of its managed service provider (MSP) meant that S.J. Louis was able to quickly mitigate the attack with zero files lost or compromised. The company had previously deployed a cloud storage gateway at each of its remote sites, serving as an all-in-one file server, backup appliance, and offsite data protection service. This enabled its IT manager to centrally manage and monitor backups of company servers around the country, configuring backups to occur every night, sending server data to the gateway, which keeps a local copy on-site and also replicates the data to the cloud for offsite protection. This hybrid backup model provided a fast-local recovery option while also replacing the need for cumbersome processes for offsite tape backup.
When ransomware infected the file server in its Texas the IT team was prepared. They simply rolled back to a previous version of its files – the day before the attack – and triggered a full restore of server files from the cloud storage gateway. The ransomware was thus removed from the system, resulting in minimal disruption to office productivity. And when a second attack occurred days later, the same process was followed to mitigate another potential disaster.
The only way to put an end to this pandemic is by building the right safeguards that eliminate enterprise vulnerability and end the need to pay cyber-criminals to retrieve access to your data and your systems. S.J. Louis was recovered quickly and without paying a dime – thanks to the backup services that were in place.
Countermeasures to fight back against crypto-malware
Secure your perimeter to minimize the chance of breach
- Patch your operating systems and keep your operating systems up to date
- Train employees on ransomware and their role in protecting the organization’s data
- Disable macro scripts from office files transmitted over email
- Limit access to critical and rapidly-changing datasets to only need-to-know users
Back up all files and systems to avoid paying ransom to recover from crypto events
- Backup your endpoints, back up your file servers
- Implement lightweight, optimized data protection tools that minimize recovery points
Roll back to most current data using sync
- Mitigate a ransomware attack by combining enterprise-grade data protection tools with file sync technology to deliver an event-based business continuity solution that minimizes the blast radius of any malware attack.
- Use very granular file sync and backup procedures to minimize your recovery points to as little as five minutes – versus 24 hours or more with alternate measures.
With the right data protection tools, organizations can successfully save themselves from paying hundreds of thousands of dollars in ransom and minimize the period of business outage. Make sure you’re prepared, it’s the only way to survive and prosper in this landscape of radically heightened threats.
Jeff Denworth, SVP Marketing, CTERA for itproportal.com | Photo credit: Pixabay


0 Comments